Top 10 Security Mistakes Your Users Make
At Synergy Technical, we know that October is Cybersecurity Awareness Month. To get ahead of the curve and keep you informed, we're focusing on cybersecurity in September. To kick off our cybersecurity month, we want to make you aware of ten security mistakes that may put your company’s security at risk. But all hope is not lost -- many of these mistakes can be partially avoided by implementing the right policies.
#10 Keeping your screen unlocked when walking away
For those that work in the IT field, this may seem like an obvious one. In the past, you may have even sent a silly email to a user’s boss so they would get “the talk” about locking screens and never forget after that day. But sometimes a quick chat can turn into an impromptu meeting and a device is left unlocked for an hour.
The fix: for Windows devices, you can set your PC to automatically lock when you step away from it using your phone’s Bluetooth, or use the handy ctrl+alt+del. For MacBooks, you can enable a hot corner that locks your screen, or use third-party software to have a similar Bluetooth-based auto-lock like Windows.
#9 Writing their password down
Ah, the sticky note on the desk — or monitor, or “hiding” under the keyboard or file cabinet. I guarantee more of your users have their password written down than you’d like to think. With how complex our passwords need to be to outsmart all the cybersecurity risks, it is understandable that people need help remembering, but that doesn’t mean written passwords are okay.
The fix: user education is the only true fix, but there are a few systemic changes you can make to help your users. By using Seamless Single Sign-on, users will only be prompted to sign in once and afterwards can access many different applications. Encouraging users to have a passphrase can help with memory, as it’s more relevant than a random alphanumeric combo but more secure than a password. Enabling a policy that prevents common passwords can help reduce risk as well. Finally, you can enable self-service password reset so users can easily reset their passwords in the event that they do forget.
#8 Reusing passwords
Have all my negative points about passwords convinced you to try passwordless yet? Anyway, reusing passwords for multiple applications is bad, and reusing them for many years is even worse. Even if your password is complex, a data breach can reveal your password, and you may not know that a breach has occurred. For most users if the hacker has one password they have all passwords, which sets you up for a world of hurt.
The fix: Seamless Single Sign-on means your users will have less passwords and therefore less risk. Of course, multi-factor authentication adds an extra layer of protection, too. You should also create policies to enable password expiration dates, so users are forced to create a new password. And please, don’t just add a number to the end of your existing password.
#7 Storing files locally
By storing files on the device rather than in a corporate cloud such as OneDrive, users are opening the company to a few different security risks. The first one is that in the event of malware, malicious actors will have a much easier time accessing files stored on a desktop. Similarly, this can open a device up to ransomware if the company needs those files and the only copy is on the computer. In the cloud, your data can be replicated making the device just one location of many copies. It also can be harder to control files on a device, and as a company you always want full control over your sensitive data.
The fix: implementing Windows 365 Cloud PCs creates a seamless Windows experience from anywhere and keeps all your company data in the cloud. Another option is blocking downloads in SharePoint and OneDrive, but the files must be in view-only mode.
#6 Giving away details on social media
I have harped on this since the day I got into security, and I will never stop spreading the message – STOP doing those “what was your first car” quizzes on Facebook as well as those games “answer these 10 questions and we’ll tell you what season you are.” They are prime data-harvesting opportunities and many of those questions are you giving away answers to common security questions or even possibly your password!
Employees also may accidentally give away sensitive information about the company in other ways, like making videos of office tours that show access points (we’ll get into social engineering soon, don’t worry…) or divulging sensitive information in a public space.
The fix: I would love to tell you that there’s software that blocks your employees from posting security risks online, and there may be some all-encompassing software that can help, but that is just not feasible. It starts with hiring responsible employees that understand the importance of keeping confidential information confidential, and then consistent reminders to not share information. User training can help employees identify what’s not safe to share, because it really is hard to know sometimes, but best practices is to keep work information at work.
#5 Falling for phishing emails
We all know phishing is on the rise, and I don’t need to give you a bunch of scary statistics to prove it. One point I really want to make here is that phishing emails have become so hard to detect. It’s important to not blame the end user 100%.
The fix: ensure you have the proper protections in place. The first step is stopping malicious attachments and emails from getting to your employees by using Microsoft Exchange Online Protection and Microsoft Defender for Office 365. Then, in case an email breaks through those filters, also have security policies in place to limit the blast radius. And, of course, user education is a must. We have solutions that give you real-time feedback on how knowledgeable your users are and can give targeted training to those users.
#4 Never restarting, updating, or powering off
Just like a nap doesn’t replace a good night of rest, setting your computer to sleep doesn’t do the same things as a power off/restart. Oftentimes a power off also enables smaller security updates that you may not see. Don’t forget that updating operating systems is a must. Many zero-days are fixed by software updates, so not updating leaves your systems open to critical vulnerabilities. There is a reason that when you bring a device to a help center, their first question is “have you tried turning it off and turning it back on again?” Restarts clear the memory which stops any tasks using your RAM and can help fix internet connections, and even boost performance!
The fix: you can set group policies to configure automatic updates and controls after reboots. This forces the users to update their systems to stay secure and compliant.
#3 Accessing unnecessary company information
Many users have access to more secure data than they should, whether they know it or not. Even if they are not visiting those files or services, if a hacker gains access to that user’s account, they too would be able to see important internal information. There is no benefit to giving extra users access to data, and the impact can be huge.
The fix: because of how critical this can be, Microsoft has many options in place to ensure you’re following least privilege access best practices. There are many different levels of admins so that you can be very granular with what each user has access to. You can also set admin privileges for only a short period of time in case another employee is out, and you need an admin just for the week. We get that it can be tricky to implement all of the right policies and protections, so we offer a security assessment to help make sense of your security posture.
#2 Using a personal device to access company data
We all have Microsoft Teams & Outlook on our devices, right? We have to make sure we didn’t miss a Teams chat from the boss while we were away from our computer! Having corporate applications on personal devices is incredibly convenient, but also comes with some nasty security risks. If your business is not controlling a device and it signs into your internal systems like SharePoint or Teams, you don’t know who just gained access to your system. The device could have malware, spyware, or be using a dangerous Wi-Fi network.
The fix: luckily, the fix is easy. You could, of course, give everyone corporate phones, but that can get expensive quickly. The cheaper & more convenient option is to enable Microsoft Intune on personal devices. You’re only managing corporate applications so there are no privacy risks, but the company is able to ensure the safety of corporate data.
#1 (Accidentally) clicking on ads or malicious sites
It can be incredibly difficult to decipher which websites are malicious, or which “download” buttons may be fake. In the image below, you may be able to see the word “Advertisement” under a few of the download buttons. However, if you’re in a rush and are trying to convert a file from PDF to Word, you may click the first button you see. Not only is this website an example of bad patterns, it’s also malicious. Web-based attacks are on the rise, so clicks have become even more dangerous.
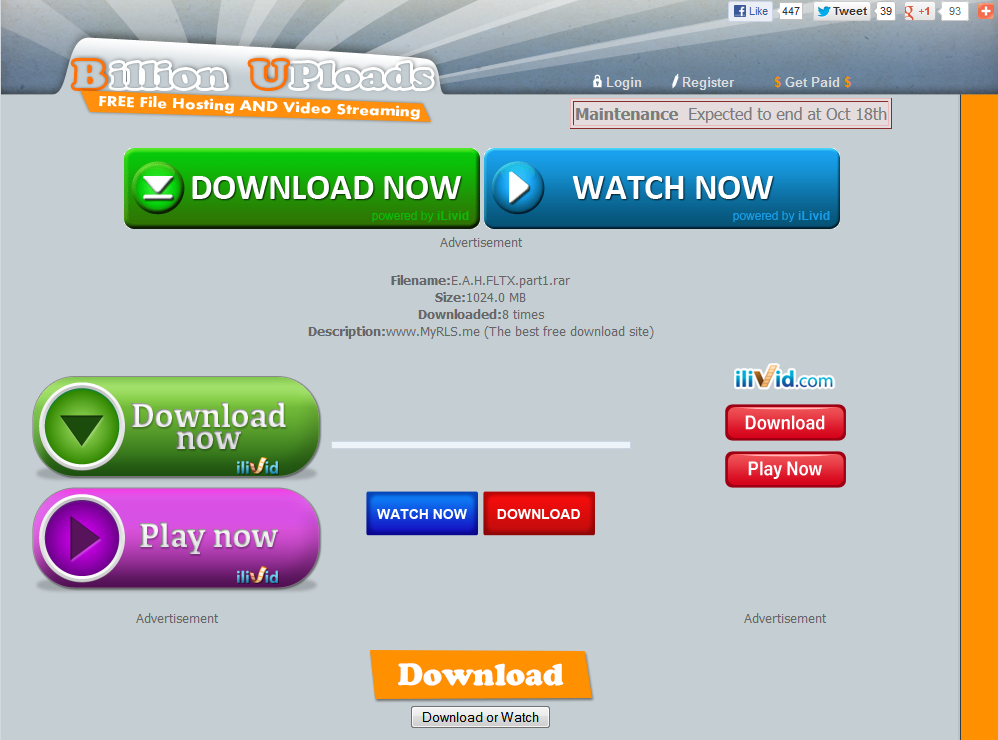 The fix: broken record alert; user education is the way to go. Block access to these bad sites whenever possible, but you can’t out-policy users from clicking hidden ads or convincing ads on websites. Microsoft also has many offerings to protect your network and prevent employees from accessing dangerous domains.
The fix: broken record alert; user education is the way to go. Block access to these bad sites whenever possible, but you can’t out-policy users from clicking hidden ads or convincing ads on websites. Microsoft also has many offerings to protect your network and prevent employees from accessing dangerous domains.
Key takeaways? User education is the underlying factor in all ten of these security mistakes. There are many tools to help you redirect users and protect against their actions, but new threats will continue to pop up and it will take time before a fix is in place. Invest the time, energy, and resources into teaching your users what to look for, and you won’t have to spend your time reading scary blogs like this that tell you what your users are doing wrong.
Comments