
turn everyday conversations into signals that prevent misconduct and regulatory penalties
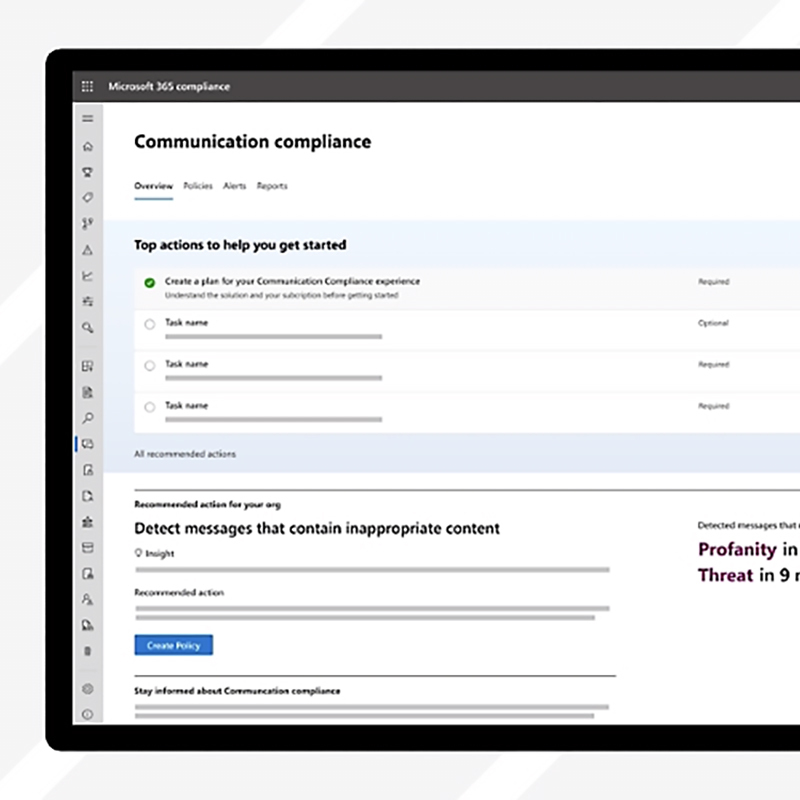
implement microsoft purview communication compliance
Collaboration tools multiply the ways employees share ideas, yet each new channel creates fresh exposure to regulatory fines, data leaks, and workplace misconduct. Hybrid work and BYOD policies blur the line between sanctioned and “off-channel” messages, while regulators now expect firms to supervise email, chat, voice, and even AI-generated content. Without a clear strategy, compliance teams drown in manual review and IT struggles to plug gaps across disparate systems.
Spot risky communications, prove compliance, and prevent data leaks with Microsoft Purview Communication Compliance
What is Microsoft Purview Communication Compliance?
Purview Communication Compliance is Microsoft’s cloud solution for detecting, investigating, and remediating risky or non-compliant communications across Microsoft 365 and connected third-party platforms. It solves three core business problems:
- Regulatory exposure: Captures and supervises electronic messages to satisfy rules from bodies such as the SEC, FINRA, HIPAA, and public-records laws.
- Insider threat and data leakage: Surfaces early signs of sabotage, bribery, or unauthorized disclosure before damage occurs.
- Workplace conduct: Identifies harassment, discrimination, or toxic language so HR can intervene quickly and uphold company culture.
What can you do with Purview Communication Compliance?
Here’s how Purview Communication Compliance translates its promise into everyday value: the capabilities below plug straight into your Microsoft 365 environment and give your teams instant, actionable oversight across every communication channel.
Launch supervision quickly without building complex keyword lists with AI-powered policy templates
Out-of-box classifiers detect misconduct (stock manipulation, harassment, gifts and entertainment breaches).
Ensure no critical conversation slips through the net with multichannel coverage
Monitor Microsoft Outlook, Teams chat and meetings, Microsoft 365 Copilot prompts, plus connectors for WhatsApp, Slack, and SMS.
Balance compliance oversight with employee trust and GDPR requirements with role-based, privacy-first review
Anonymize user identities and enforce granular reviewer permissions with full audit trails.
Cut manual triage time and speed issue resolution with investigation and remediation workflows
Flag messages, highlight risky terms, route cases, and let reviewers delete, notify, or escalate from one dashboard.
Give security teams a 360-degree view of potential insider incidents with Purview Insider Risk Management integration
Combine communication signals with file movement, device activity, and behavioral analytics.
Provide leadership with evidence of diligent supervision and continuous improvement with actionable reporting.
Pre-built dashboards track policy matches, trends, and false-positive rates; export data for auditors.
Ready to learn more? Discover how to implement Microsoft Purview Communication Compliance
Deploying and configuring Purview Communication Compliance touches IT architecture, legal policy, licensing, and employee privacy. Our consultants map policies to your regulatory obligations, clarify which Microsoft 365 and add-on licenses you need, connect third-party channels, fine-tune classifiers, and train reviewers on best-practice workflows—giving you maximum protection with minimal disruption. Book a Purview Communication Compliance consulting engagement today to build a smooth rollout plan and start capturing risk from day one.
How can Purview Communication Compliance help your organization?


Reduce regulatory risk
Keep email, chat, and voice traffic under continuous supervision with pre-built regulatory classifiers. Each potential violation is bundled into concise, audit-ready cases, giving your compliance team the evidence and trend reports needed to satisfy FINRA, HIPAA, and similar mandates while easing review fatigue.
Foster a safer, respectful workplace
Purview Communication Compliance watches for harassment, discrimination, or threats and alerts HR before issues ripple through team morale. Pseudonymized messages with risky phrases highlighted let your investigators coach or escalate within minutes and uncover broader conduct patterns without exposing lawful private exchanges.



Enable proactive insider-risk protection
Communication signals merge with file movements, device activity, and other behavioral analytics across Microsoft 365 to reveal intent well before data leaves your environment. Security teams gain a unified timeline that shows who referenced sensitive projects, when files were copied, and whether patterns mirror past leak scenarios—empowering early intervention to protect intellectual property.
Dive deeper into the Purview family
Manage and govern on-premises, multicloud, and SaaS data and gain a bird's-eye view on your entire data estate.
Our consulting services related to Microsoft Purview
We offer assessments, engagements, design and configuration, and more. Each resulting in a roadmap to success for your digital transformation.
How we're different
Recognitions and certifications
Synergy Technical has been accredited with several partner recognitions.

Microsoft FastTrack Ready Partner
FastTrack is a combination of resources, engineering expertise, and best practices that ensures you have the most efficient deployment and adoption possible.

Microsoft Security Workshop Partner
As a leading Microsoft Security Workshop partner, we help organizations assess their environments and strengthen protection using Microsoft's productivity and security solutions.

Microsoft Cloud Solutions Partner
Subject matter experts in Modern Work for Enterprise and SMB, cybersecurity architecture, identity and access management, information protection, and additional specializations.

Our proven experience
- Deployed over 20M seats of Office 365, Microsoft 365, and Microsoft EMS
- Customers in all 50 states
- Experience in 70+ countries

Ready to get started?
Synergy Technical has a long history of delivering successful cloud and on-premises security solutions to customers. Contact us to learn best practices on how to successfully deploy and configure Purview Communication Compliance policies while meeting your organization's security requirements.













%20Empower%20Applications-1.png)

%20Protect.png)