Windows Defender ATP
I’ve spent the better part of the past year evangelizing EMS. It’s a fantastic suite of tools that offers a huge range of controls to protect corporate assets, particularly for remote and mobile users. One of the really neat features of EMS is Advanced Threat Analytics. This one raises eyebrows every time I talk about it, and it’s fun to watch the security teams go from casually ignoring the presentation to sitting up on their elbows. If you don’t know: ATA is a fully on-prem agentless intrusion detection solution that relies entirely on AD domain controllers and port mirroring to aggregate, profile, and contextualize security threats from inside the perimeter. Mull that over: it can’t be detected because there are no agents; it captures literally EVERYTHING that touches your network from AD-connected devices, since they are always talking to DC’s; it has the ability to read AD attributes and decide if two similar activities from two different users is a problem; and it only surfaces things that stand out as irregular. That’s a huge amount of power.
But as I was extolling the virtues of ATA to a client just a few weeks ago, one member of their security team asked, “what about payloads that don’t interact with the network?” Oh. Well. I guess we’ve just found a limitation, and it’s a valid one, too, because if the payload doesn’t reach out to network resources, it’s going to go undetected. There are payloads that begin with traversing local resources, and there are business travelers that spend huge amounts of time away from a protected network. There is a gap: ATA cannot protect them.
But hope is not lost! With the Windows 10 Anniversary Update came notification of a new solution, Windows Defender Advanced Threat Protection. The name was confusingly similar to ATA, and there seemed to be no real way of enabling it, so most folks promptly ignored it. But I managed to get invited to join the closed beta program, and I showed it off today for the office.
That gap? It’s gone.
Windows Defender ATP is an odd little product. It doesn’t (yet) directly integrate with ATA, Intune, SCCM, or really anything else. Its agent is more similar to a SCOM/OMS agent. But an agent it is, and it reports back the same types of activity as ATA to the Windows Security Center…running in Azure…sort of. As of right now, it appears to be a single global tenancy with no other features. Once logged in, MS has conveniently placed logs from a virtual system into the service so you can see what sort of behavior to expect, but they also included steps to enroll a system of your own.
Prepare for a sea of caveats, because…
-
It must be a Preview Release of Windows 10
-
Though there is a deployment package available for Windows Intune, it doesn’t work
-
You can’t do anything with it from your current tenancy
-
The dashboard is…rudimentary, at best
But I just so happen to have a Windows 10 Preview client, and after downloading the configuration script, I was able to see my machine and look back over an activity timeline that looked very similar to that of ATA. And while my machine surfaced no issues (yay!), the test virtual system appears to be infected. I haven’t spent a ton of time trying to create suspicious activities, but in looking through the data that has been surfaced, I can see and track outside IP’s my machines have accessed, and drill down into those IP’s for information about who owns them and how much interaction they have with my environment.
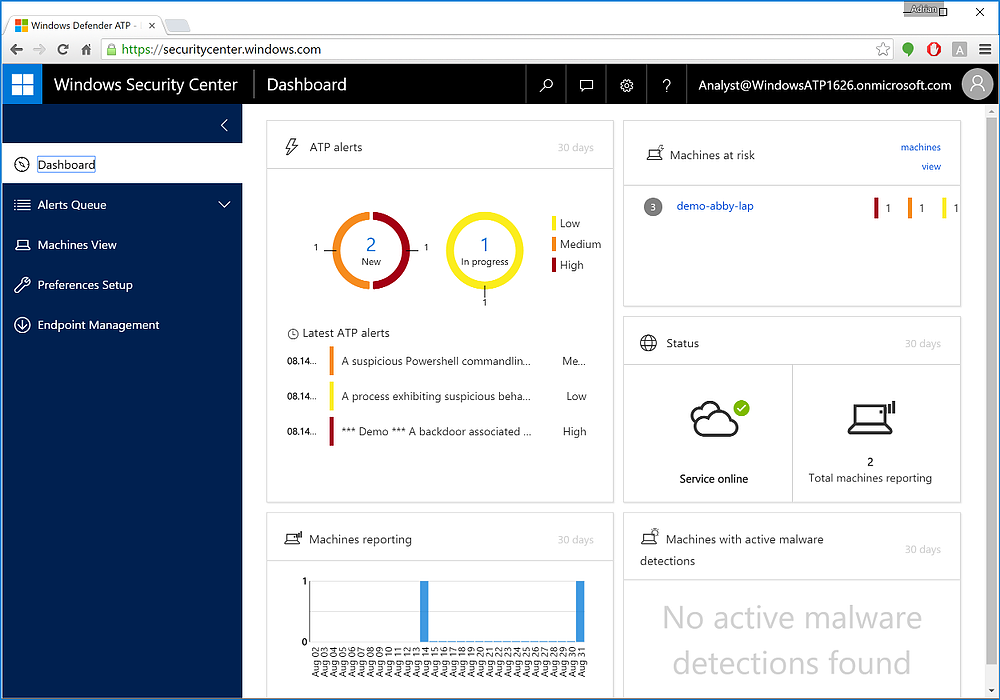
Figure 1 The default dashboard shows at-risk machines, alerts, malware, and service health. And you can't change that right now. Also, note that this is a MS-owned tenant: ATP cannot be accessed from a customer tenancy.
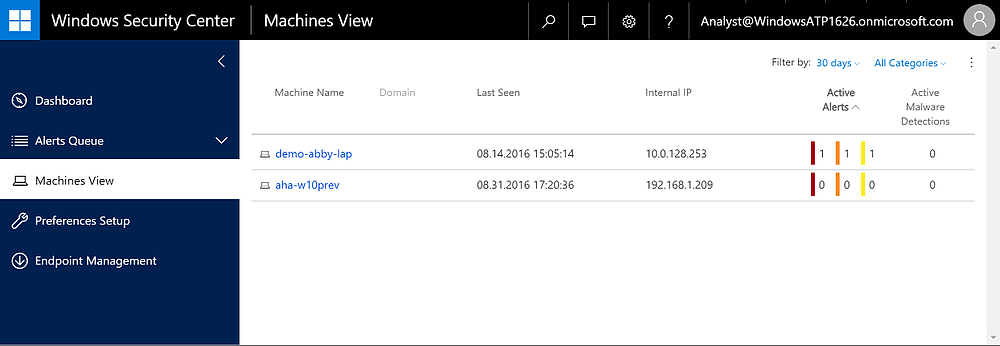
Figure 2 Machines view shows alerts per machine and how long it's been since they last reported home.
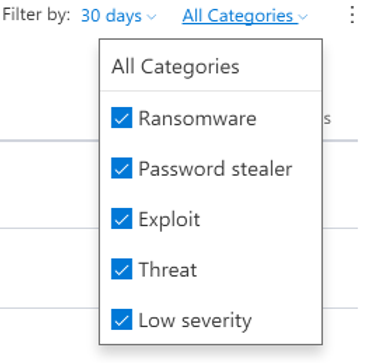
Figure 3 Machines view can be tweaked slightly to show specific detection categories.
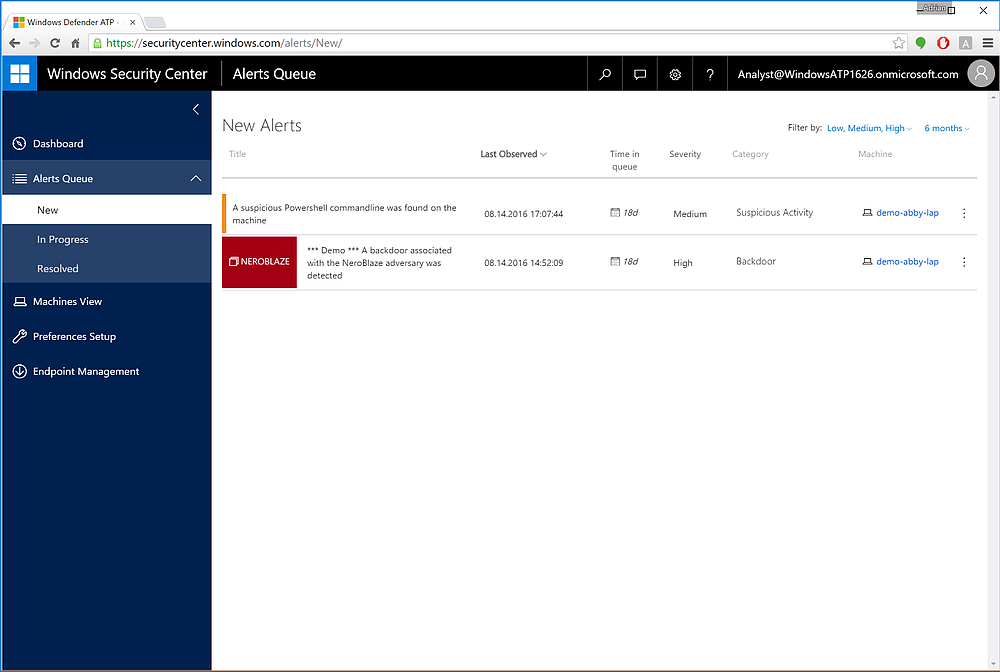
Figure 4 Microsoft includes this sample attack detection, along with associated machine activities and how long ago the issue was first detected.
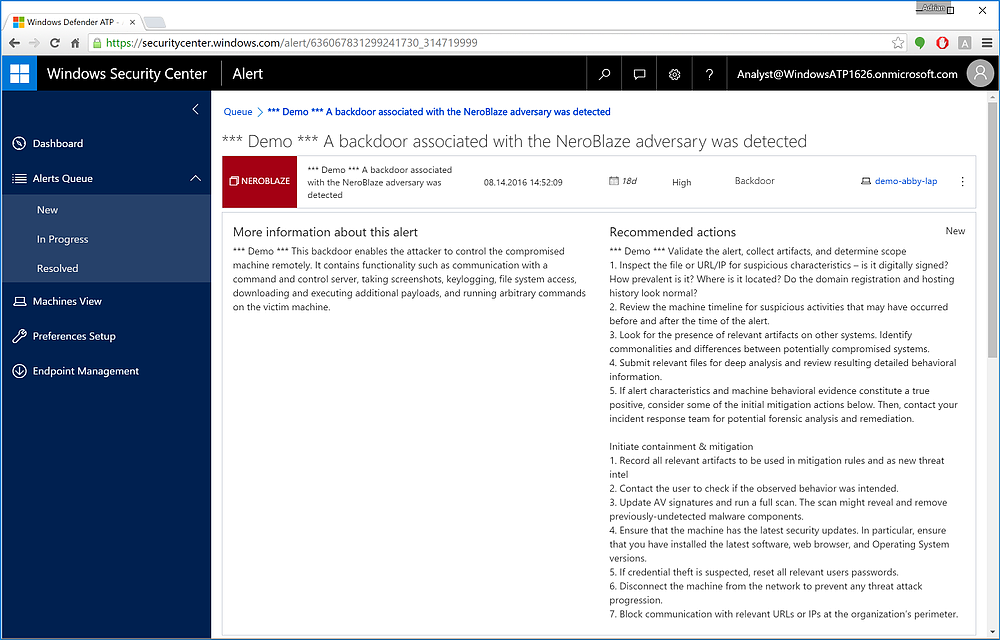
Figure 5 Drilling down into the sample attack reveals a wealth of information about the specific attack detected, along with recommendations on containment & mitigation. Note that ATP cannot actively resolve the attack or its vector.
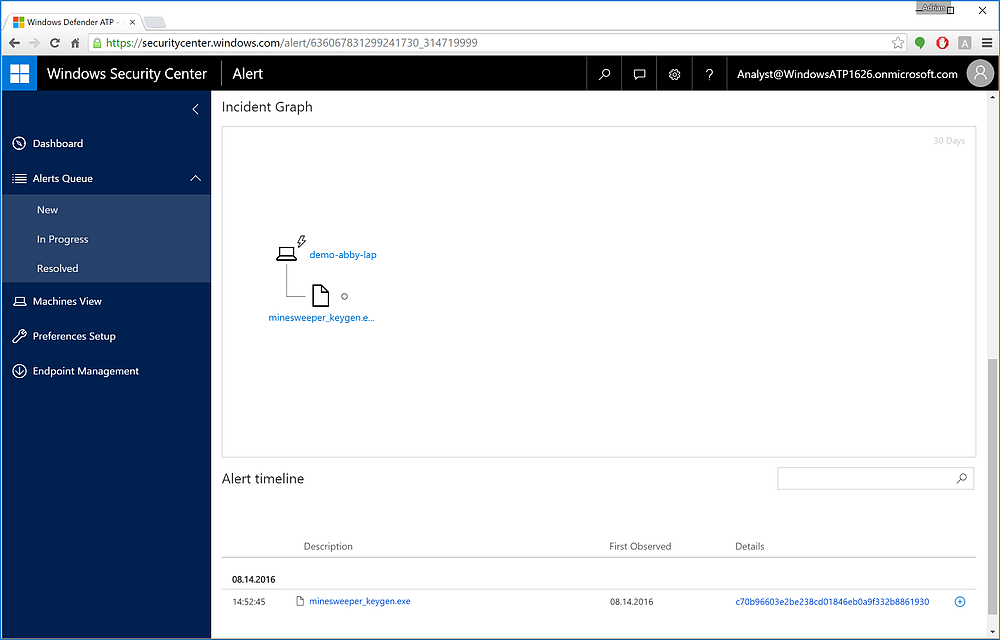
Figure 6 Not tremendously interesting with just one machine reporting, but the Incident Graph will show a prevalence of the attack within the organization if multiple machines report in with the same issue. The same holds for the timeline.
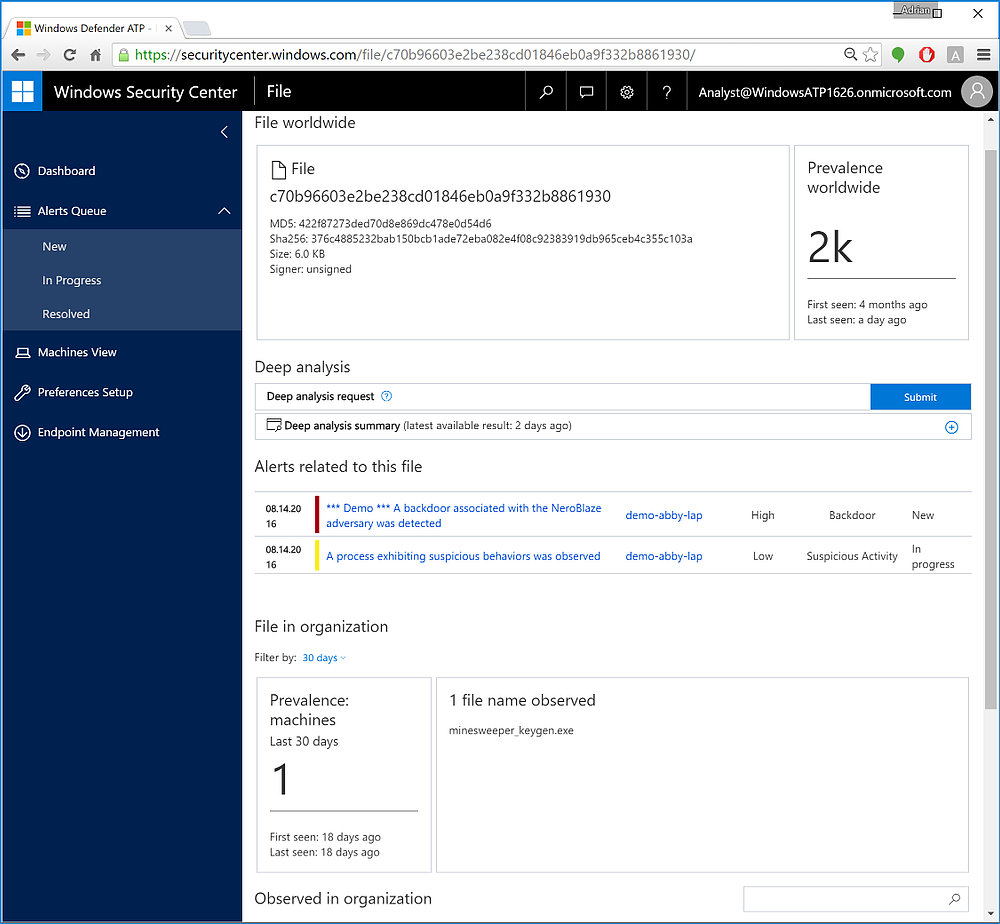
Figure 7 We can also drill down into the file name itself for global reporting data and deep analysis options.
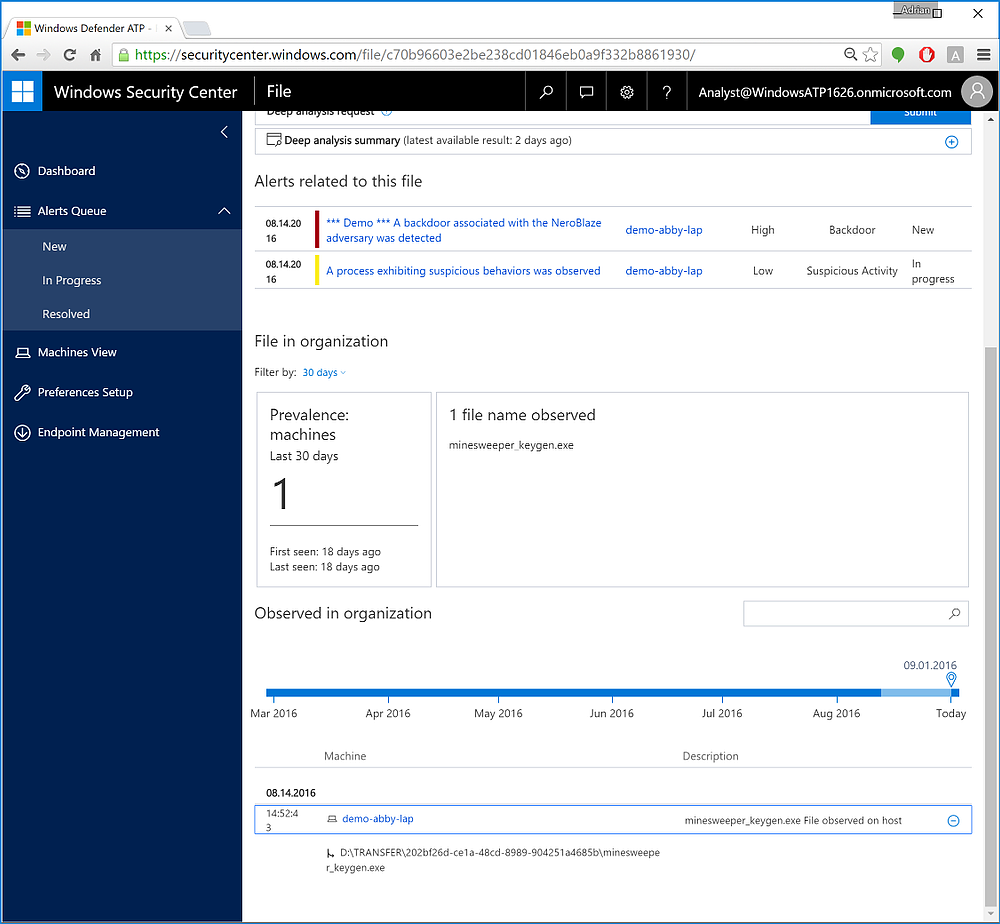
Figure 8 And helpfully, we can also get the file PATH on the infected host(s).
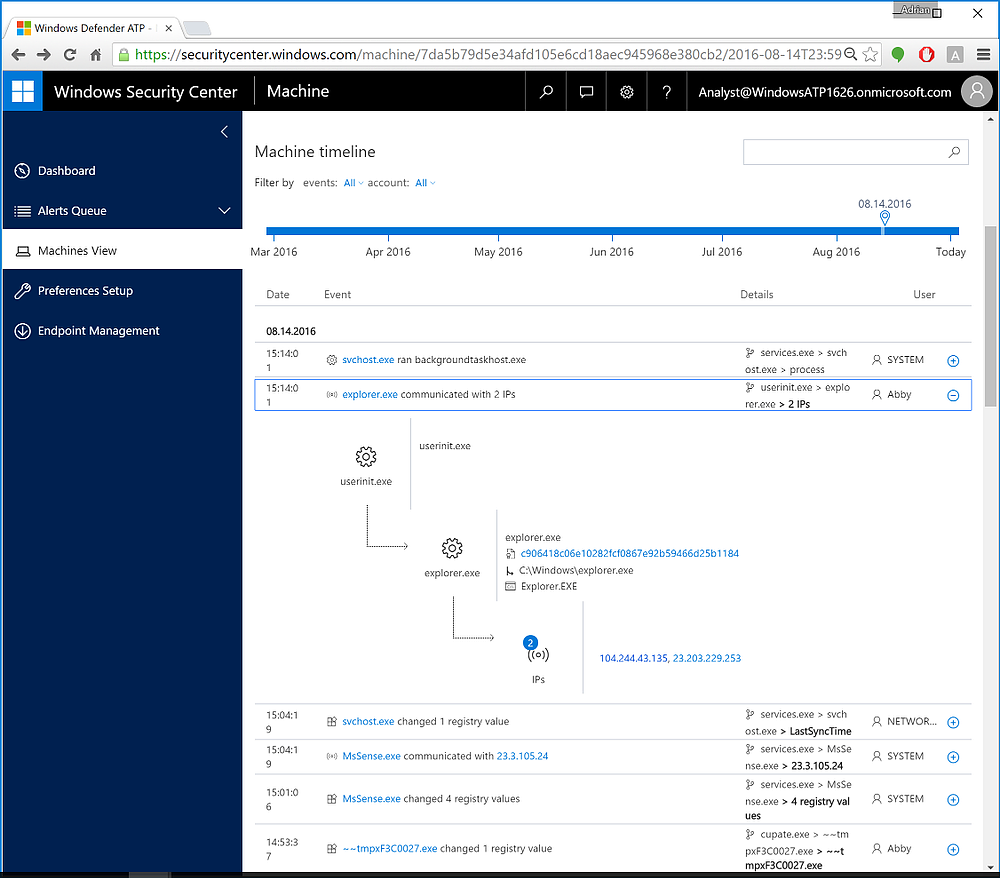
Figure 9 Unlike looking at security logs, ATP (like ATA) parses security activities into events. We can drill down into these events to see processes and interactions. What are those IP's?


Comments