Latest Microsoft Weekly Round-Up

Last week we had our monthly webinar on Compliance Manager, which got some nifty new features that made it into the blog that had been published earlier in the month. Well the hits just kept coming, and Microsoft issued official guidance on using Azure AD to meet Zero Trust & MFA requirements as part of their NIST & FedRAMP configurations and address the Executive Order on Improving CyberSecurity.
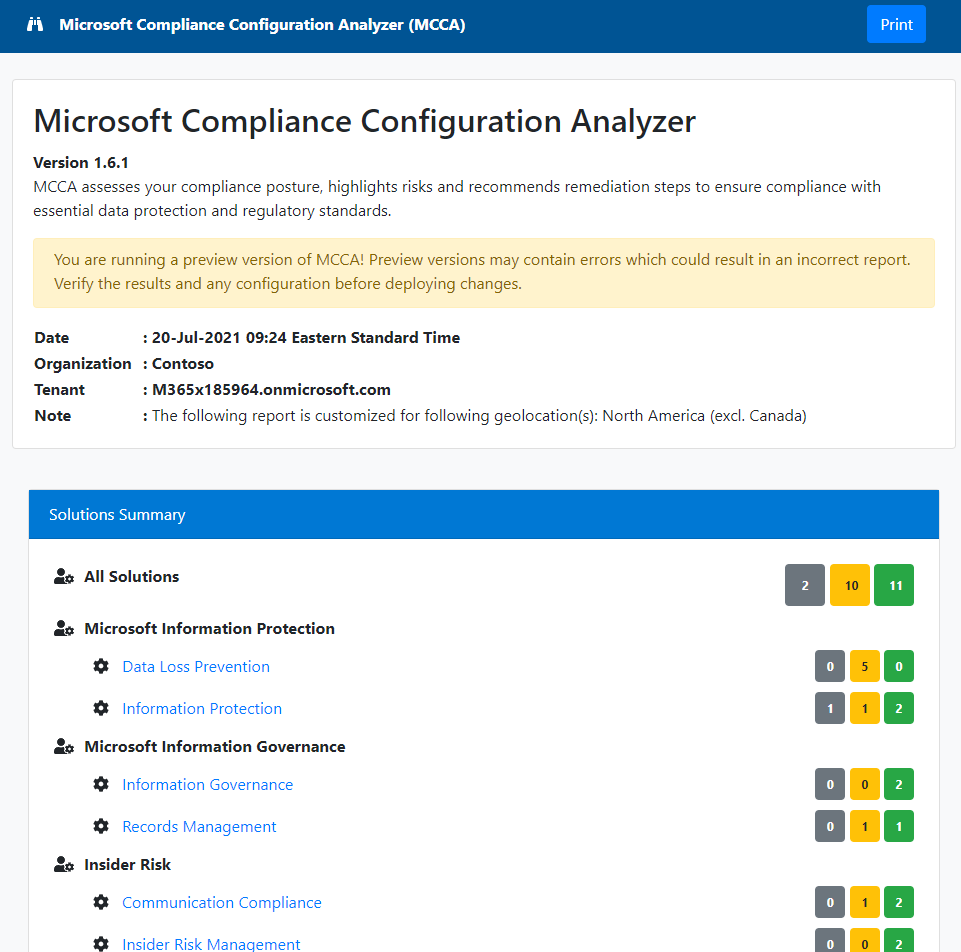
But wait: there's more! As part of a quick-start solution to Compliance Manager, Microsoft has also published a Compliance Configuration Analyzer. It's in Preview and runs in PowerShell, but analyzes your Azure environment and puts together a lovely web-based report that differentiates between recommendations and improvement actions. You need to run the report with an account holding the 'Compliance Admin' role to get everything, but you're using RBAC & the principle of least privilege, right? Right? The tool can also query by geography. Think of this as pre-gaming your Compliance Manager experience.
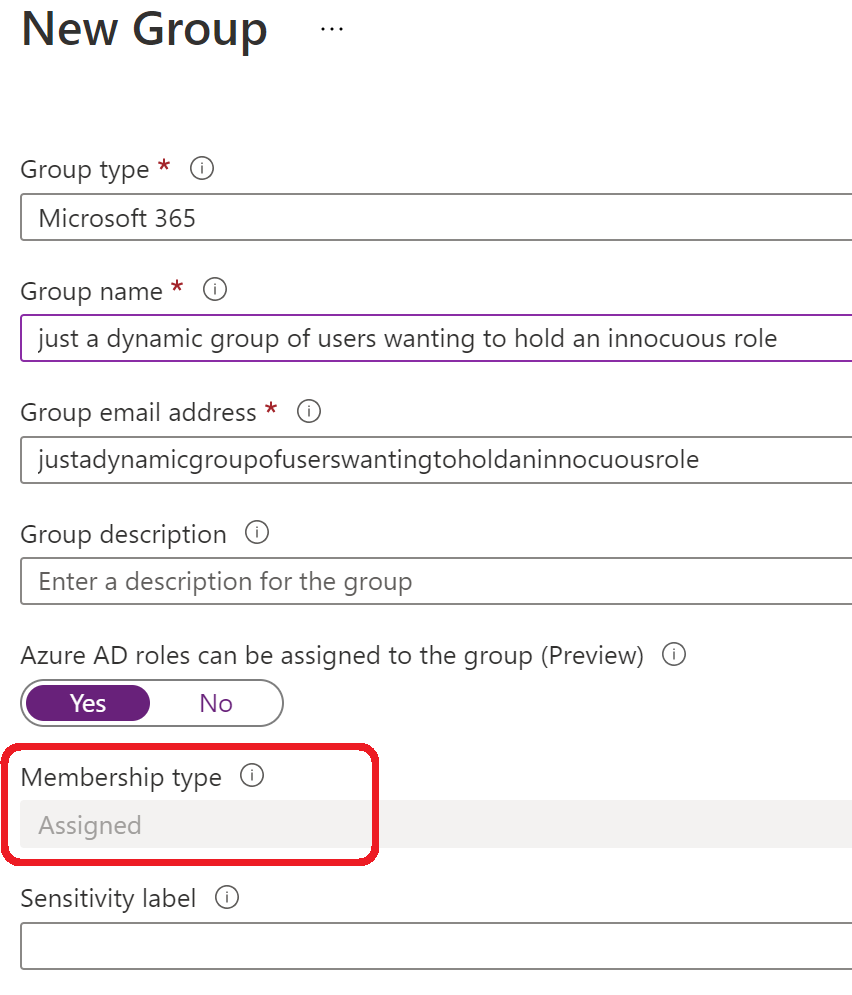
Have you played around with Attribute Based Access Controls? I'm a big fan of management by attributes and good directory hygiene, and currently Azure RBAC doesn't allow dynamic user groups to be assigned Azure AD roles, so this is an area I hope to see developed a LOT in the future.
A common question I get is whether or not Intune can prevent data loss through removable media. Yes, it can, but now Defender for Endpoint is in on the game, too! Now we're moving into the granular control space by first identifying what's connected with Advanced Hunting, then tailoring our policies from there. This should allow us to avoid the "break first then allow" administrative fist of doom. Then we can define specific allowed/blocked actions, alerts, and responses.
Autopilot customers know it, but it comes as a shock to many others that Intune integrates directly with the Microsoft Store for Business. Windows 11 aficionados have been buzzing about a revamp to the Store for weeks, and the news will affect both camps: the current incarnation of the Microsoft Store for Business is going away Q1 2023. Time to start planning your redeployments, especially if you have Intune connected to deliver apps from the Store. And that's not all: the current incarnation will not support Windows 11 at all--that goes to the new store experience, which will preview in H1 2022, with GA forecast for H2 22. Ever wanted a curated list of incident response tools?
Identity Governance is my super jam, but right now its controls don't scale beyond Azure and Azure-SSO-enabled applications. Is Privileged Identity Management slated for a big hybrid/Azure-ARC style boost? Signs point to yes! If I'm day-dreaming, I'd like to see roles for all managed clouds (including private) orchestrated and monitored through a single pane of glass with automatic remediation. That would include Azure roles, some of the workload-specific roles that don't report to PIM today, along with on-premises PAM. Can't wait to see where this goes! I'm calling a 5-internet-dollar bounty on the first person who finds an over-arching admin role, permanently assigned to "Authenticated Users", called something ridiculous like "Mjolnir", to entirely defeat the purpose.
Speaking of hybrid identity management, there's a new version of AAD Connect out! And I mean a new version: not just an incremental update. In fact it will not install as an update, because there are some fundamental differences in protocol support (TLS1.2), authentication libraries (MDAL vs. ADAL), and sing it from the mountaintops: no more reliance on Global Administrator*! There's other stuff, too, like a requirement for PS5.0, additional attributes, and a bunch of fixes. Want to know which version you're using? That's now reported to AAD for every export. Don't forget to update your fail-over environment. (*except for SSPR configuration).


Comments