Goodbye EMS, Hello EM+S
Last week I rambled on and on in a webinar (view the online recording here), talking about all the finer points of Microsoft’s latest iteration of the mobility suite EMS. Nutshell: new name, new feature set, new set of rack prices.
Everything that’s been available in EMS remains available in the new Enterprise Mobility + Security E3 SKU. Price remains unchanged at $8.75/user and the product remains an incredible bargain with a great feature-set.
Newly-announced features like Privileged ID Management and Cloud App Security, along with enhanced features of Azure Active Directory Premium and Rights-Management (itself rebranded Azure Information Protection), get rolled into the new EM+S E5 SKU, set to drop later in Q3 2016 at $15/user. E5 gets all of the features and capabilities of E3.
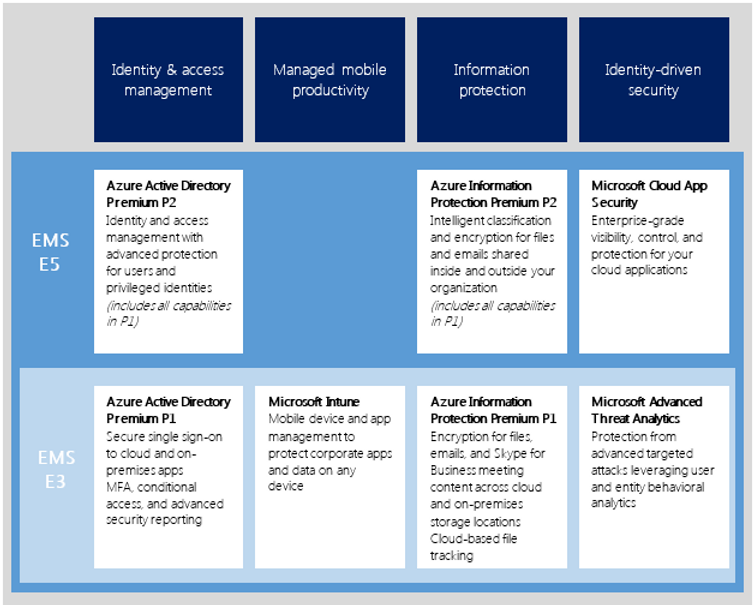
Today we’re going to stick to the left-hand column of the chart: Azure Active Directory Premium P2.
I’ve spent the last couple of months exploring these new service offerings, and they offer an incredible amount of visibility into what was already a pretty robust set of services.
We recently had an engineer take a trip overseas to a part of the world that’s not known for Internet safety. There were some concerns about him taking his corporate laptop, even with all of our faith in the cloud. 3 days after he landed, I got an email the likes of which I’d never seen: Azure had identified login requests from his account coming from his travel country, and from a system 10K+ miles away in the US. The activity had been flagged under the built-in “impossible travel time” rule, as the two logins were within 30 minutes of each other. I sent him a quick note and he was able to confirm that he had initiated both sessions: one from his machine, the next through a Remote Desktop session in an Azure datacenter.
Additional automatically detected Identity Protection risk events include: leaked credentials; sign-ins from infected devices, anonymous IP’s, IP’s with suspicious activity, and unfamiliar locations; and lockout events. Some of these reporting capabilities are carried over from the soon-to-be-deprecated Azure AD Anomalous Activity Report.
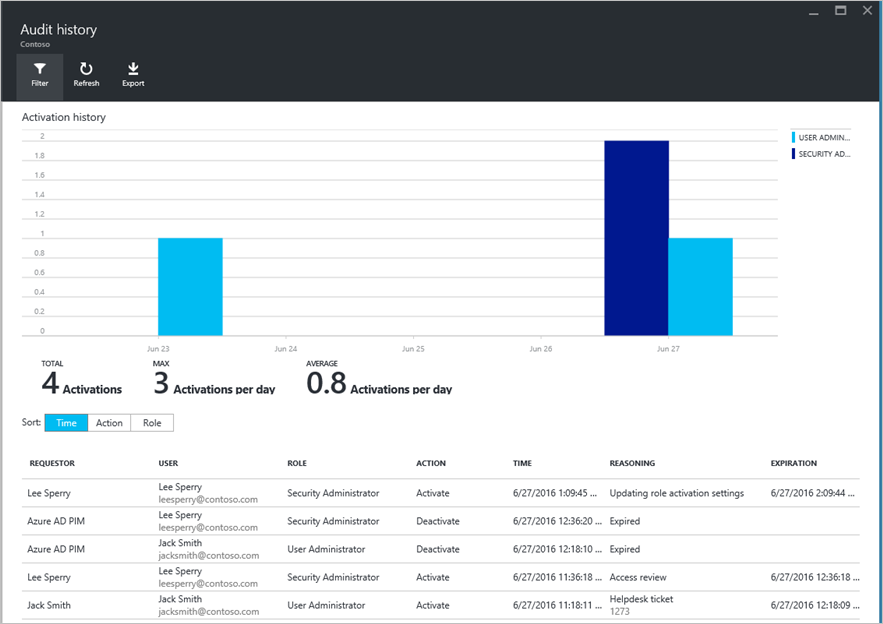
Then a few weeks ago I explored some of the capabilities of Privileged Identity Management, first having Azure run an audit of privileged accounts within the organization, then following up by dropping some users’ permanently-assigned administrative rights to “eligible”, where the user doesn’t have their admin access until they request it for a job-related activity. I then followed that up by having Azure send requests to administrators within the organization confirming their administrative needs, and finally configured an audit alert when any new administrative access is granted.
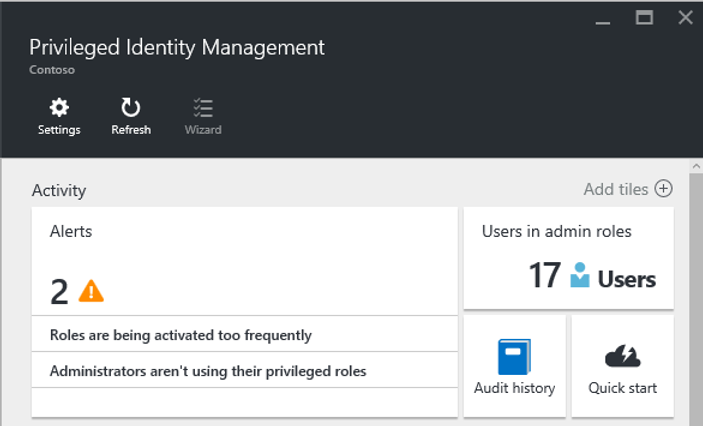
In the webinar, I spoke to the challenges of keeping track of administrative access. I’ve worked in large organizations with IT departments that spread across the globe, and in almost all instances, the only time you know who has admin access in the organization is when you’re going through an audit. Without advanced tools in place, you are exceedingly unlikely to get notified of privilege elevations. Azure’s new EMS E5 offerings, particularly in Azure AD Premium, handle these tasks with ease, surfacing information automatically to configurable dashboards and alerts, and providing instant reporting with history, including reporting on how often those administrative accesses are not just requested, but also actually used.
Finally, it’s worth noting that Microsoft is making a strong push for both single sign-on and to eliminate the password as the weakest link in a user or organization’s security posture. With multi-factor authentication and full licenses for Microsoft Identity Manager (MIM), one single identity can now extend from your on-prem datacenter to Azure, to Azure’s SaaS partners, and to your federated business partners. We’re finally reaching a point where that sticky note under the user’s keyboard doesn’t grant malicious access to your corporate data.


Comments