A Security-in-depth approach to limiting mal- & ransom-ware attacks
See the full interactive Sway
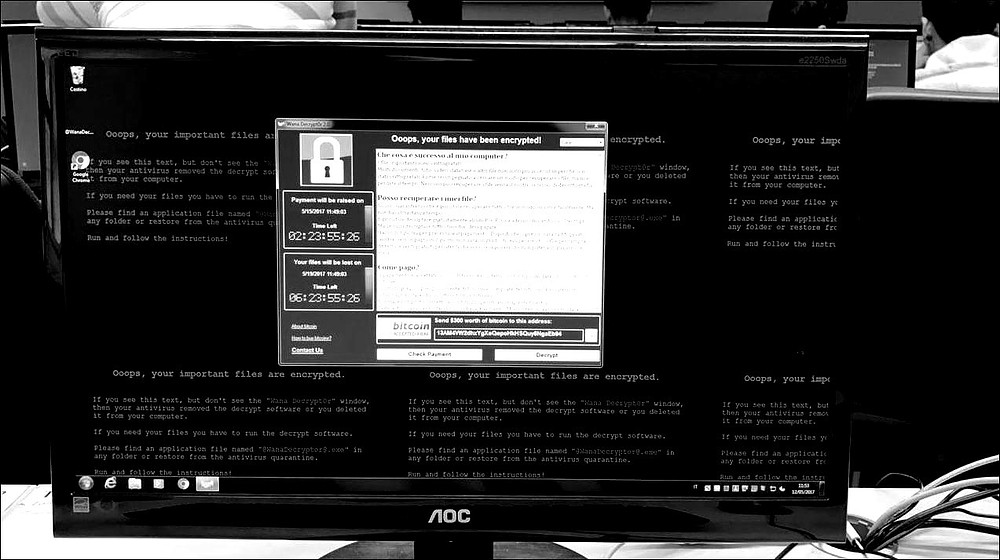
Last week was pretty tough for a large segment of the IT community. The British National Health System was just one of a number of high-profile targets that resorted to physically unplugging critical systems to prevent data-loss. But in many cases, by the time data-loss was detected, it was too late. Attackers have become more adept at exploiting our perimeters, sure, but they've also figured out our typical response cadence, and now build their attacks to infiltrate, enumerate, pause, and detonate. During that pause, secondary infections take root and it's a rinse/repeat cycle until the payload detonates.
What can we do?
It's no real secret that several security products were bested by this most recent round of attacks. Vendors can only protect against known signatures and attack vectors--new approaches take time to build the necessary detections, and unfortunately that often means widespread infections. And there's no single solution that can absolutely guarantee our safety. Given the way last week's attacks unfurled, via malicious links in e-mail, we would have to ensure that every e-mail service and every e-mail client our users access is protected or restricted in some meaningful manner, be it through proxy solutions or CASB-integration or even just good ol' user training (a critical but oft-overlooked element to any IT strategy).
Defense-in-depth
The concept of defense in-depth has changed dramatically over the years. In ye olden days, a big perimeter defense and a secure VPN was considered sufficient. The traditional "castle walls" approach was fine. You may have even had an IDS/IPS solution and some sort of file or storage encryption. Now, though, we have to assume a very different security posture, one of "assume breach" at all times, and that forces a different security landscape within our environment. And because that environment exists wherever the user may be, it has to be portable and flexible. I'll be the first to admit that I did not take ransomware threats seriously when they first emerged. My data was encrypted, after all! But it didn't take too long before I started seeing successful attacks against already-encrypted data. Think about it: if your data is encrypted at the disk level, the files don't know they're encrypted. Even at the file-level, a document on your hard drive can be encrypted, compressed, re-encrypted, re-compressed, and tossed in a .zip file. The file doesn't care: it just responds to what the OS tells it to do.
 An Interwoven security fabric
An Interwoven security fabric
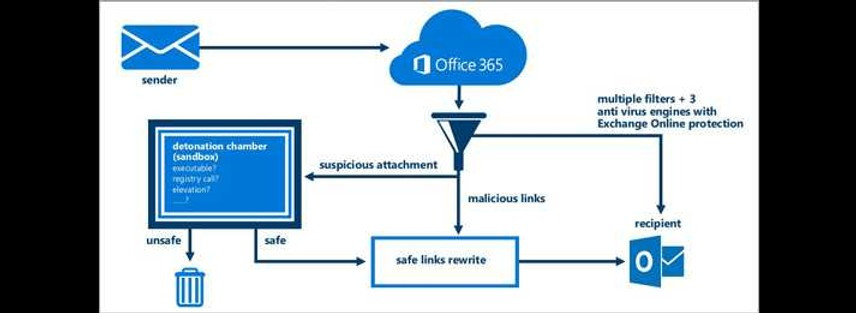
Pulling together a complete solution (again with the caveat that you can't prevent every attack with technology alone) requires having several products working together in unison. WannaCry was launched as a malicious link. Security researchers have been stating for some time that the single most effective technology for limiting attacks is link and attachment filtering: stop the attack before users can even take careless action to put your systems at risk. Advanced Threat Protection for Office 365 (a component of Office 365 E5) provides safe-link rewrites for all Office Pro Plus 2016 desktop apps, along with ensuring malicious links do not make it to the user's inbox. Malicious attachments are similarly scanned and stripped, and unknown attachments are detonated in a secure and protected sandbox in the Microsoft cloud prior to delivery to ensure no malicious code is present.
At a stand-alone Windows 10 Enterprise level, Windows Defender Advanced Threat Protection (included with Windows 10 Enterprise E5) is able to monitor a local host for suspicious or anomalous activity, which is reported to an Azure control panel and compared against that same global threat intelligence footprint to detect attacks before they can even leave the local workstation.
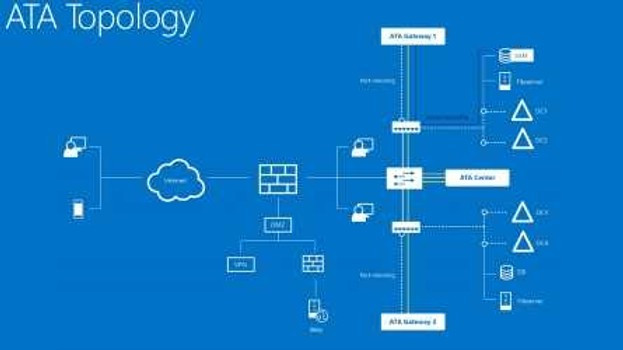
Enterprises that have an Active Directory on-premises can augment Windows Defender ATP's capabilities with an installation of Microsoft's Advanced Threat Analytics, a component of the Enterprise Mobility & Security suite. ATA listens to all domain controller traffic to profile your users and their normal behaviors over time, raising alerts only for known attack vectors or anomalous behaviors...like enumerating a network for unprotected SMB shares.
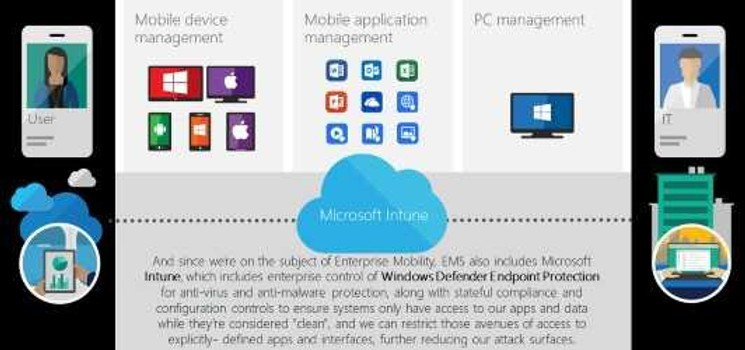
Additionally, since the #1 method for spreading the infection was through open SMB access, keeping files in SharePoint Online and using modern interaction methods like Microsoft Teams or web-based access further reduces the likelihood that your critical data will be compromised. But I mentioned way back in the beginning that no single set of tools can provide 100% protection against user error. Enterprise Mobility & Security offers a pair of tools that can work in conjunction or independently to significantly reduce the opportunity for non-corporate apps to expose us to user error. These tools are Cloud App Discovery and Cloud App Security, and in general terms, one supersedes the other. Available in EMS E3 licensing is Cloud App Discovery. This agent-based tool reports on all detected apps and interfaces that touch cloud services, and can be deployed easily to a mobile workforce. While it doesn't enable any particular controls, it does tell you what your users are doing outside your controlled cloud footprint. The big brother product Cloud App Security takes a different approach, pulling firewall or proxy logs to determine what cloud apps are in use, and then enabling API-level controls over some of the more common ones. Working together as a security fabric, we're able to leverage the power of the Microsoft enterprise stack to prevent infections from getting into our systems through malicious links, prevent anything that does get through from branching to other systems, report on anything that even tries to access other systems, shut down in-process attacks on the local system, boot the user or device out of datasets & apps, and help ensure users don't pull malicious data from other cloud solutions. And if something does manage to happen, Office 365's Security & Compliance Center notifies me of anomalous file-access behaviors extremely quickly, allowing me to enact additional interventions. One SKU, one bill. Flexible control, and logical interactions throughout the security stack.


Comments