
detect and respond to identity-based threats
deploy microsoft defender for identity
With identities now the primary target in cyberattacks, traditional perimeter defenses are no longer enough. Attackers exploit weak credentials and move laterally across hybrid environments, putting sensitive data and operations at risk. To stay secure, organizations must protect their identity infrastructure—from on-premises Active Directory to Microsoft Entra ID and beyond.
Protect user credentials, monitor privileged access, and leverage AI-driven analytics to identify suspicious behavior with Defender for Identity
What is Microsoft Defender for Identity and why it matters
Microsoft Defender for Identity is a cloud-powered security solution that detects, investigates, and responds to advanced identity threats. Built to protect hybrid identity environments, it delivers real-time visibility into user and entity behavior, detects suspicious activity, and helps stop attackers before they can cause harm.
Defender for Identity directly addresses critical business challenges:
- Reduces breach risk by detecting compromised credentials and abnormal access.
- Strengthens Zero Trust strategies by continuously monitoring privileged identity behavior.
- Saves IT time and resources through automation, intelligent alerts, and seamless integration with existing Microsoft tools.
What can you do with Microsoft Defender for Identity?
Microsoft Defender for Identity delivers powerful features designed to identify and block identity threats before they impact your organization. These capabilities offer visibility across hybrid environments, support proactive defense strategies, and reduce manual effort for security teams.
Real-time threat detection
Identifies brute-force attacks, pass-the-hash, golden ticket, and other advanced techniques targeting Active Directory.
Identity posture management
Highlights risky configurations like unconstrained delegation or excessive privileges, helping reduce attack surfaces.
Behavioral analytics
Uses machine learning to baseline user activity and detect anomalies that suggest compromise.
Integration with Microsoft Entra ID and Microsoft Defender XDR
Provides end-to-end user visibility across on-premises and cloud identities, correlating signals for faster incident response.
Automated response actions
Quickly contain threats by disabling compromised accounts, enforcing password resets, or isolating devices.
Ready to learn more? Discover how to deploy Microsoft Defender for Identity
Identity threats demand more than reactive defenses—they require strategy, visibility, and expertise. If your organization is looking to secure identities, reduce lateral movement, or advance your Zero Trust journey, our consultants are here to help. We will partner with you to assess your Active Directory environment, identify vulnerabilities, and align Microsoft Defender for Identity with your security and compliance goals. From configuration and integration to alert tuning and incident response, we bring the technical depth and business insight to make identity protection a strength—not a gap. Ready to take the next step? Let's talk about how we can support your identity security strategy.
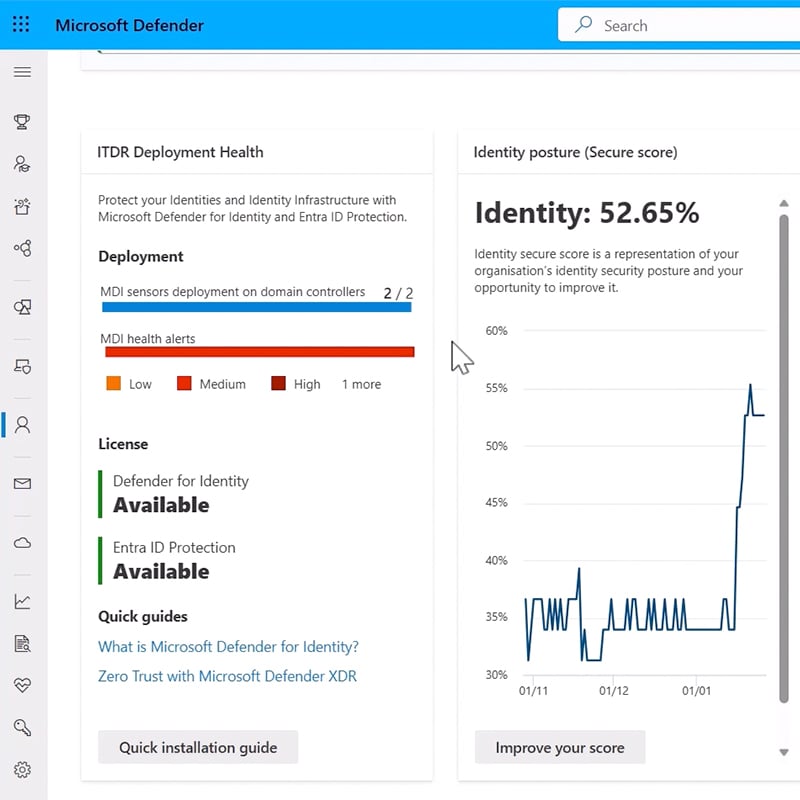
How can Microsoft Defender for Identity help your organization?


Stop attacks early
Detect identity threats before lateral movement or data exfiltration occurs—protecting sensitive assets and maintaining business continuity. With real-time alerts and insights into attack techniques like credential stuffing and Golden Ticket attacks, organizations can respond to threats before they escalate.
Unify security operations
Defender for Identity integrates seamlessly with Microsoft Defender XDR and Microsoft Sentinel, giving security teams a unified view of identity, device, and network threats. This consolidation reduces alert fatigue, accelerates investigation and response, and helps security teams operate more efficiently.



Improve compliance and governance
Continuously assess and improve identity configurations, meet regulatory requirements, and prove audit readiness through built-in reporting and analytics. Defender for Identity provides the visibility and controls necessary to comply with regulations such as GDPR and CCPA, reducing legal risk and enhancing accountability.
Dive deeper into the Microsoft Defender family
Microsoft Defender is a comprehensive suite of security solutions that helps protect your entire digital estate across endpoints, identities, email, cloud apps, and infrastructure.
Our consulting services related to Microsoft Defender
We offer assessments, engagements, design and configuration, and more. Each resulting in a roadmap to success for your digital transformation.
How we're different
Recognitions and certifications
Synergy Technical has been accredited with several partner recognitions.

Microsoft FastTrack Ready Partner
FastTrack is a combination of resources, engineering expertise, and best practices that ensures you have the most efficient deployment and adoption possible.

Microsoft Security Workshop Partner
As a leading Microsoft Security Workshop partner, we help organizations assess their environments and strengthen protection using Microsoft's productivity and security solutions.

Microsoft Cloud Solutions Partner
Subject matter experts in Modern Work for Enterprise and SMB, cybersecurity architecture, identity and access management, information protection, and additional specializations.
%20World.png)
Our proven experience
- Deployed over 20M seats of Office 365, Microsoft 365, and Microsoft EMS
- Customers in all 50 states
- Experience in 70+ countries







%20Applications%20Protect.png)
%20Computer%20Protect.png)
%20Mail%20Protect.png)


%20Empower%20Applications-1.png)

%20Protect.png)
